CRIMJ304:
Lesson 1: The History and Development of Security
Introduction
Lesson Overview
The purpose of this lesson is to introduce you to the long history of security, and how, through the ages, that history has shaped the development of the private security profession. To begin, the chapter defines security, which is followed by a discussion of how early societies sought to achieve individual (for self) and collective (for the community) security. Following this, the lesson provides a detailed description of the foundations of the private security profession in America. On the whole, this lesson is critical for understanding the connections between the origins of the need for security and the ways in which the security profession has matured. The discussion highlights the fact that security remains a key element of one's quality of life as highlighted in Maslow's well-known "Hierarchy of Needs," in which security is presented as the second layer of his pyramid (See Figure 1.1). In fact, in post-9/11, national security or homeland security represents one of the most pressing concerns of the 21st century. This, too, will be highlighted in the course.
Figure 1.1 Maslow's pyramid
Lesson Objectives
By the end of this lesson, you should be able to:
- Define the concept of security;
- Trace the historical development of security from ancient times to the present;
- Understand the move toward professionization of private security;
- Understand the scope and nature of Private Security in America.
Please complete readings and assignments as listed on the course schedule.
What is Security? And What Are Its Origins?
Security can be defined in a variety of ways, but one very good definition of it is provided by Fischer and Green (1998): "Security (italics in original) implies a stable, relatively predictable environment in which an individual or group may pursue its ends without disruption or harm and without fear of disturbance or injury" (p. 3). For thousands of years, individuals and societies have pursued security, which has been accomplished in a variety of ways. In addition, security has taken on both public and private forms. Charles Reith provides the following four phases that illustrate the development of security concerns:
- First, individuals or small community groups came together in search of collective security, to ease food finding or to satisfy other mutually felt individual needs;
- Second, they discovered the need for rules or laws. Historically people believed that passing "good" laws was sufficient; the ruler's army could enforce them;
- Third, they inevitably discovered that some community members would not obey the rules. Even the best laws people can devise are useless, and rulers and governments are powerless, if the laws are not obeyed.
- Fourth, in one form or another, means to compel the observance of rules were found and established. Sometimes they worked, but frequently they did not. Consequently, more communities have perished because they could not enforce their laws than have been destroyed by natural disasters or hostile aggression (as presented in Hess & Wrobleski, 1996, pp. 2-3).

Figure 1.2 Caveman Protecting his home
Among the variety of measures used to ensure security, Hess and Wrobleski (1996) aptly point out that rulers used "weapons, lakes or cliff dwellings, walls and gates." Thus, they made use of the natural and enhanced landscape to ensure their security. In ancient times people such as the Sumerians made use of private security forces and bodyguards to provide security. Fortresses were also popular in ancient times. The Great Wall of China, for example, was built between 220 BC and 200 BC. It was build to protect the Chinese from their enemies. Built of earth, stones, wood, and later, bricks, it stretches 4,000 miles and has walls over twenty feet high, to go along with a walkway that is more than fifteen feet wide. Besides the wall itself, an additional security feature was watch towers. These towers were used to "store weapons, house troops, and send smoke signals" (Wikipedia, 2007).

Figure 1.3 Great Wall, Watch Tower, Castle, and Fort
The Egyptians used intricate tombs to provide security for the treasures often buried with Pharaohs. Of these, Tutankhamen's, whose treasures have been part of a global tour for the past few decades, is the most famous one. Figure 1.4 illustrates the interior structure of King Tut's tomb. The figure reveals that while robbers did penetrate the tomb at various points in antiquity, the design of the tomb successfully kept them from reaching the treasury.
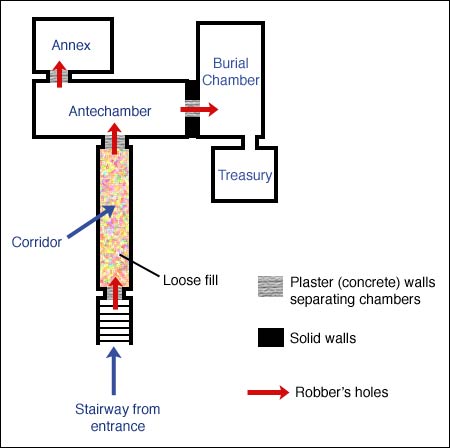
Figure 1.4 Interior Structure of King Tut's Tomb
Knowledge Base
 Reading
Reading
- The assigned reading is Chapter 1 in the Dempsey's Introduction to Private Security.
- Download and review the PowerPoint slides for Chapter 1.
Learning Activity
 Thought-Povoking Discussion
Thought-Povoking Discussion
Now that you have learned about the history of security and the measures that have been used to provide security, think about the following:
- What measure do you take on a daily basis to ensure your own personal security?
- What security measures are being used in your neighborhood to ensure collective security?
- Looking at your responses to questions 1 & 2, provide linkages to the security measures first used in ancient times.
Post your thoughts to the Lesson 1: Security Measures discussion forum. (You will find the discussion forum in the Lesson 1 Activities folder.)
Summary
Taken together, the materials presented in this lesson sought to introduce you to the origins of security and the ways in which it has been achieved. From the very beginning, security has been about developing ways to protect self and society. But, over time, people have also sought to protect land and other material assets. To do so, they have used innovative security measures. In general, though, caves, architectural advances, gunpowder, locks, armored cars, spying techniques, and transportation advances have all played a role in ensuring security. Moreover, African, Asian, European, and American histories are all intertwined with the development of these security-related technological advances. Today, these technological advances continue, but, as you can see from the contents of this lesson, they still owe a large debt to ancient societies.
In America, while citizens, for good reasons, continue to focus on the security provided by public policing (e.g., state and municipal police), private security has a rich history and remains an area in which billions of dollars are invested each year. This investment has led to the call for more oversight and, as a response to this often pungent criticism, an increased emphasis on professionalizing the field. A review of the private security industry is presented in Lesson 2.